Azure AD Hybrid FIDO2 Security Key Sign-in
A short version of using an Azure AD hybrid with security keys and group policy for Windows 10 logon.

Azure AD has recently introduced FIDO security key sign-in for Windows logon. Microsoft has a plethora of documentation around this, but it can be confusing to navigate. The following is a down and dirty guide of how to enable FIDO2 sign-in for Windows in the Hybrid AAD environment. The following guide assumes that your Windows machines are running Windows 10 greater then version 2004 - 20H1 and are AAD hybrid joined. We will be using Group Policy to configure Windows, to allow security key sign-in.
Enable Security Key Registration
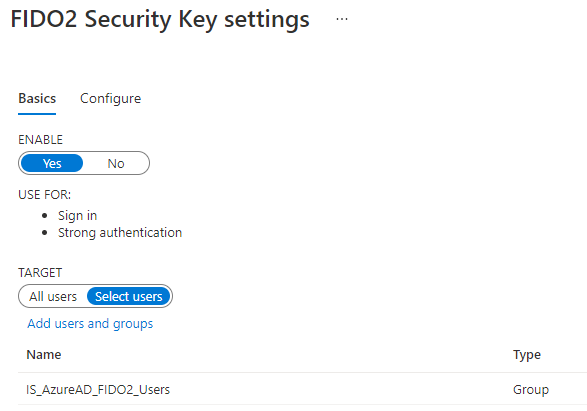
First, we will configure Azure AD to allow users to register FIDO2 credentials with their AAD accounts. In our example, we created an AD group with users we wanted to allow registration for.
- Connect to your Azure Active Directory admin center.
- Select Azure Active Directory > Security > Authentication Methods > FIDO2 Security Key.
- Select Yes to Enable, then configure a target user or group.
Register Security Key
Next, we need to register the security key to the account in Azure AD.
- Using the account you would like to configure, login to Microsoft Security Info.
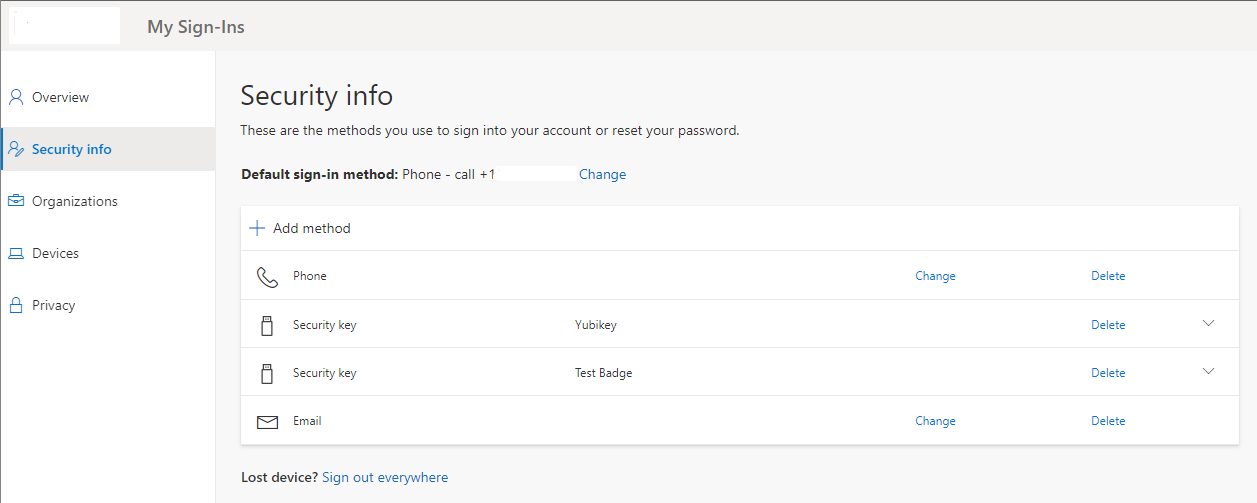
2. Select Add Method, Security Key, then Add.
3. Click USB or NFC Device (from my testing, it doesn't seem to matter which option you choose, if the security key is capable of both, either choice will work).
4. Select Next, OK, OK, then insert your FIDO2 credential.
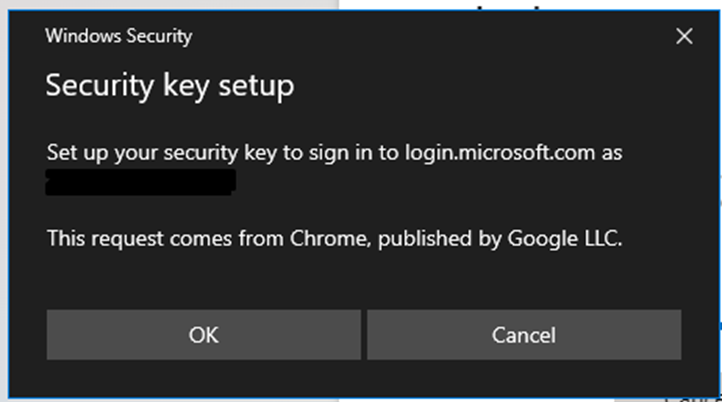
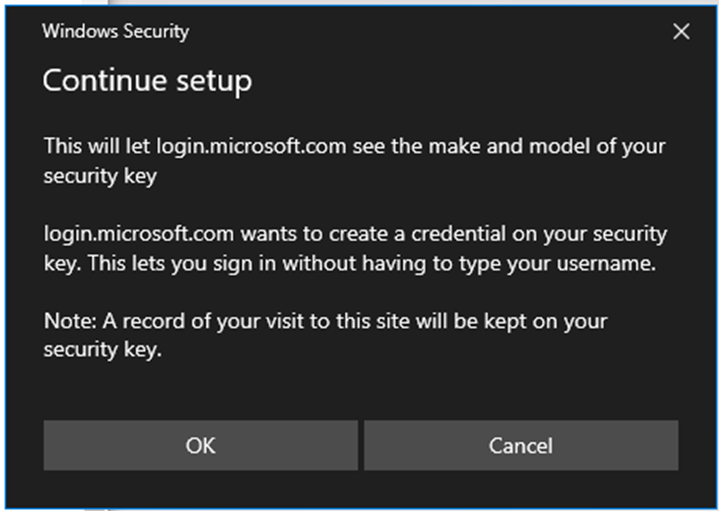
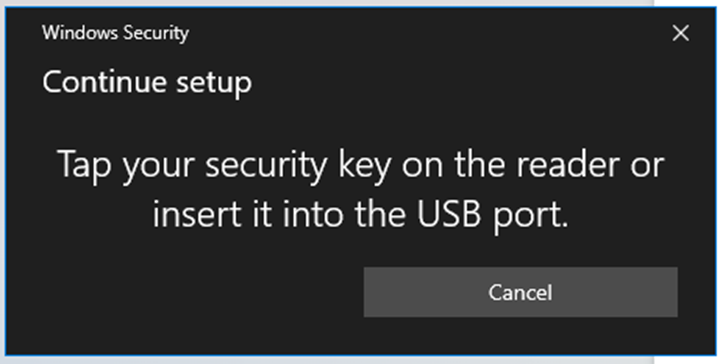
5. If you have already configured a PIN for the device, you will be prompted to enter the PIN, if not, you will be prompted to create a new PIN.
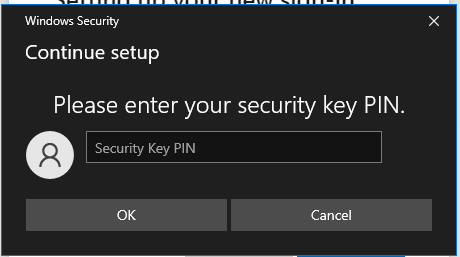
6. Once you complete the PIN authentication, you will need to name your security key. This can be used to identify it when you have multiple devices.
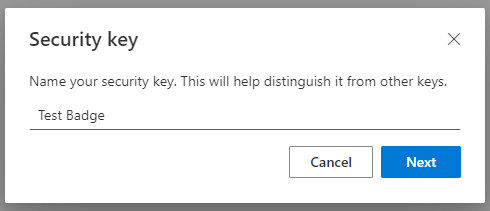
That's it! The security key has been registered successfully.
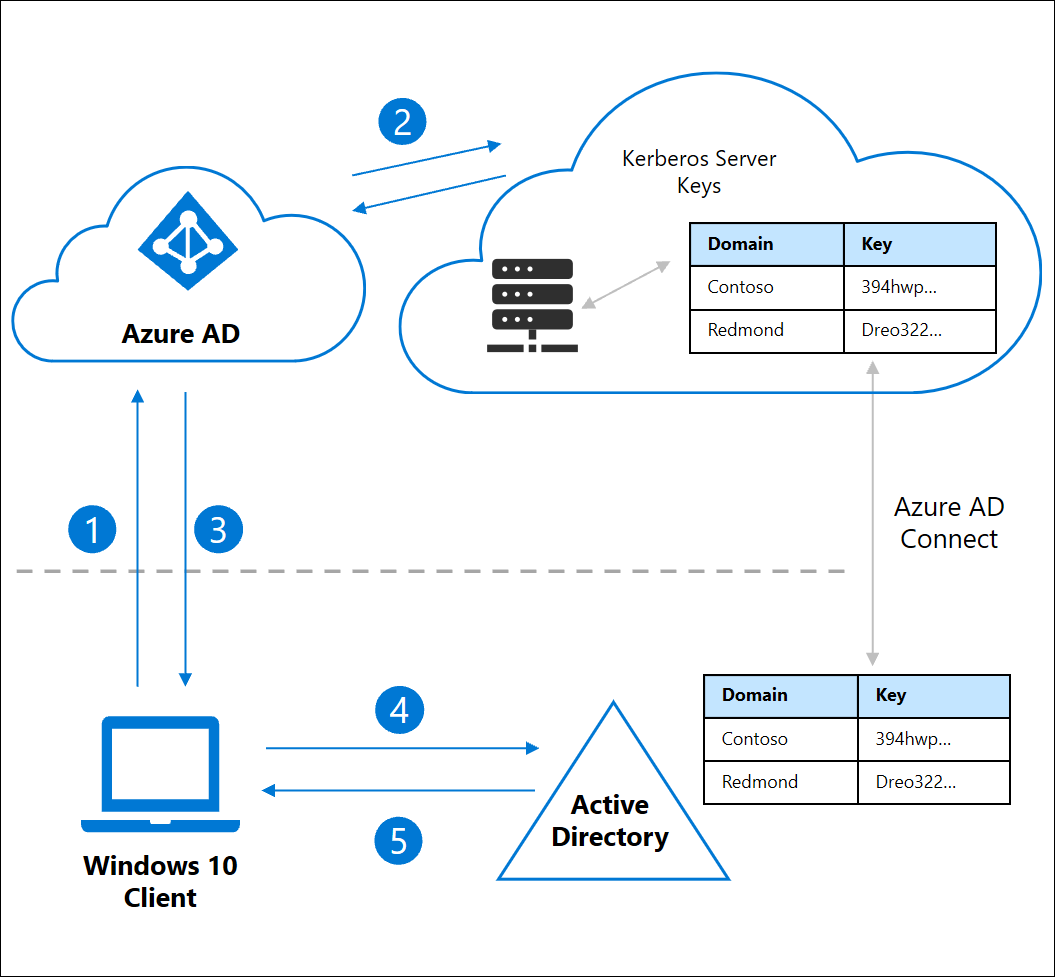
Extending on-premises Kerberos realm to Azure Active Directory
Because the machines will be authenticating against AAD, we need to extend the Kerberos realm to enable ticket granting rights. A key is then derived and securely pushed to Azure AD via Azure AD Connect.
- From your Azure AD Connect server, open an elevated PowerShell console and import the AzureAdKerberos module.
Import-Module "C:\Program Files\Microsoft Azure Active Directory Connect\AzureADKerberos\AzureAdKerberos.psd1"2. Validate that your domain hasn't already been extended using the following command:
$domainCred = Get-Credential
$cloudCred = Get-Credential
Get-AzureADKerberosServer -DomainCredential $domainCred -CloudCredential $cloudCred -Domain Contoso.com
Id :
UserAccount :
ComputerAccount :
DisplayName :
DomainDnsName :
KeyVersion :
KeyUpdatedOn :
KeyUpdatedFrom :
CloudDisplayName :
CloudDomainDnsName :
CloudId :
CloudKeyVersion :
CloudKeyUpdatedOn : 3. Extend your realm to AAD via the following command:
Set-AzureADKerberosServer -DomainCredential $domainCred -CloudCredential $cloudCred -Domain Contoso.com4. Running Get-AzureADKerberosServer should now return information about the connection.
Get-AzureADKerberosServer -DomainCredential $domainCred -CloudCredential $cloudCred -Domain Contoso.com
Id : 22973
UserAccount : CN=krbtgt_AzureAD,CN=Users,DC=Contoso,DC=com
ComputerAccount : CN=AzureADKerberos,OU=Domain Controllers,DC=Contoso,DC=com
DisplayName : krbtgt_22973
DomainDnsName : Contoso.com
KeyVersion : 147955
KeyUpdatedOn : 2/18/2020 7:53:12 PM
KeyUpdatedFrom : AADC01.Contoso.com
CloudDisplayName : krbtgt_28974
CloudDomainDnsName : Contoso.com
CloudId : 28123
CloudKeyVersion : 139655
CloudKeyUpdatedOn : 11/22/2021 9:09:18 AMConfigure Windows for Security Key Sign-in using Group Policy
While Microsoft Intune can be used to configure Windows, environments containing SCCM may find it challenging to implement the Intune policy. Thankfully, Microsoft also provided a GPO. Don't forget to update your GPO central store to find this setting.
- Create a new Group Policy Object and link the GPO to the appropriate computers OU.
- Edit the GPO, and configure the following setting.
Computer Configuration > Administrative Templates > System > Logon
Turn on security key sign-in: Enabled
That's It! You should now be able to authenticate using your security key!
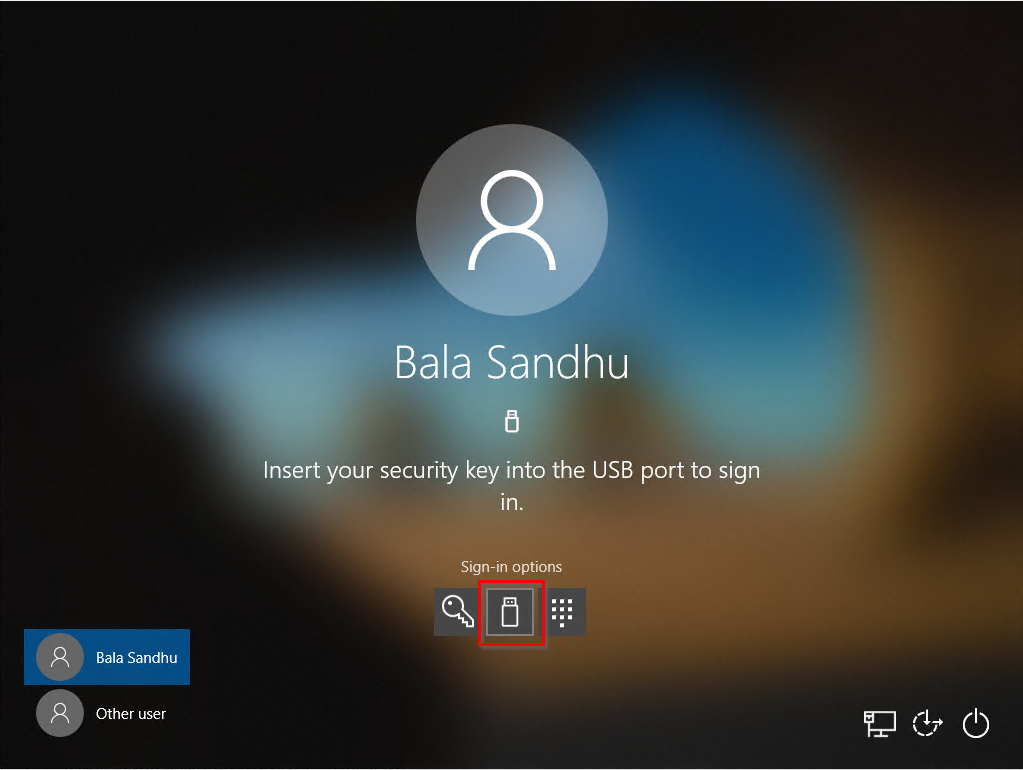
When testing with GETAC laptops with integrated HF readers and multi-technology FIDO2 credentials (HID Crescendo C2300), we identified an issue with a conflict between the smartcard and FIDO2 credential providers. To resolve this, we added the following GPO.
Computer Configuration > Administrative Templates > System > Logon
Exclude credential providers: {8FD7E19C-3BF7-489B-A72C-846AB3678C96}
Microsoft has posted a blog with much more detail on how this all works here.
Documentation on Azure AD Kerberos can be found here.





